Featured Article : What Does “Right-To-Repair” Actually Mean?
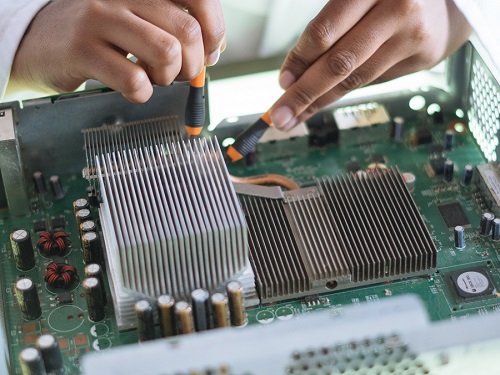
In this article, we look at the right-to-repair movement, where it comes from, and how it’s progressing. The Right-To-Repair The ‘right-to-repair’ is a movement that seeks to have rules/legislation passed that forces manufacturers (e.g. of appliances, electrical products, white goods and more) to make parts (and information) available to end customers, not just approved/authorised repairers,…
Read more